Unless You Do These Things First
Company budgets are now being firmed up for 2023 and, as the frequency, severity, and cost of cyber-attacks increase dramatically, it’s no wonder that enterprise demand for cyber insurance has also skyrocketed.
But, while cyber insurance may seem like a relatively easy way for a company to plug in gaps in security, it just doesn’t work like that anymore. Insurers have not only raised premiums (by an average of 174% in 2021), but they’re also tightening security requirements before initiating or renewing accounts.
Why? Because insurance providers, seeing the increase in high-profile cyber events, have realized that risk and potential for payouts are just too high and, in the end, your risk becomes theirs.
Otherwise put, the cyber insurance industry has become a bit like health insurance in that you pay more (or get rejected) if you have a pre-existing condition. The pre-existing condition, in the case of cyber insurance, is poor cybersecurity. What used to be a relatively short application process has been stretched to several pages and countless questions about how secure you already are.
Your Cyber Ducks in a Row / What insurers require BEFORE you can renew or obtain a policy
Here’s how to get your security controls up to snuff so you can minimize cost and stay ahead of tough cyber insurance standards.
Multi-Factor Authentication (MFA) Across the Board
MFA is no longer just a nice-to-have. Following the White House executive order last year and a mountain of expert advice on the importance of MFA, insurers have followed suit. Many are demanding that companies implement MFA for all endpoints, privileged accounts, and even remote access.
In one example, applicants are required to answer yes to the following:
- Is MFA required for all employees when accessing email through a website or cloud-based service?
- Is MFA required for all remote access to the network provided to employees, contractors, and third-party service providers?
- In addition to remote access, is MFA required for the following, including such access provided to third-party service providers:
All internal and remote admin access to directory services (Active Directory, LDAP, etc);
- All internal and remote admin access to network infrastructure components (switches, routers, firewalls); and
- All internal and remote admin access to the organization’s endpoints/servers.
And it goes on …
Please describe any circumstance where MFA is not used and any mitigating controls in place. If MFA is not in place, what is the timeline for full deployment of MFA on all applications?
What percentage of applications are not using MFA?
- Are any of these applications critical?
At the very least, employ MFA across your network and all surfaces that might be exposed to threat actors. Points of exposure include privileged accounts within your network as well as cloud and SaaS-based applications.
Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR)
EDR can be deployed to detect threat and protect individual endpoints or devices, while MDR provides monitoring and management of your company’s entire IT environment. It is not uncommon that an MDR provider also offers EDR solutions as a part of the service.
Updates and Patches
You will be required to document updates and patches. The need has become more urgent over the past couple of years because of the increased frequency and speed of cyber events.
Backups and Recovery
Insurance providers require that businesses have current backups in a separate, secured location. Backups should also have MFA to restrict unauthorized access and should include a solid disaster recovery plan.
Incident Response Plan
You will be required to have a documented and tested incident response plan in place that includes the steps you’ll take with the insurance provider, IT, legal team, public relations, and your customers.
Employee Training
As always, human error is the weakest link when it comes to cyber threats. According to reports, 26% of cyber incidents in 2021 were due to insider crime, while 74% were caused by employee negligence or phishing – resulting in the theft of login credentials. Insurers now require that staff is trained to use proper “cyber hygiene” and to identify threats.
In summary, setting up a controls-focused approach to security is no longer just the “smart thing to do”. In the short run, it’s the best way to save your company money and headaches. But in the long run, a strong security posture is going to be required of all businesses.
But is Cyber Insurance Worth the Cost?
There is no easy answer. There are no guarantees when it comes to cyber-attacks today. But what is absolutely certain is that the Best Insurance is YOUR OWN STRONG CYBERSECURITY POSTURE.
Before making the decision to apply for a policy, you’ll need your cyber ducks in a row.
Here’s how we can help
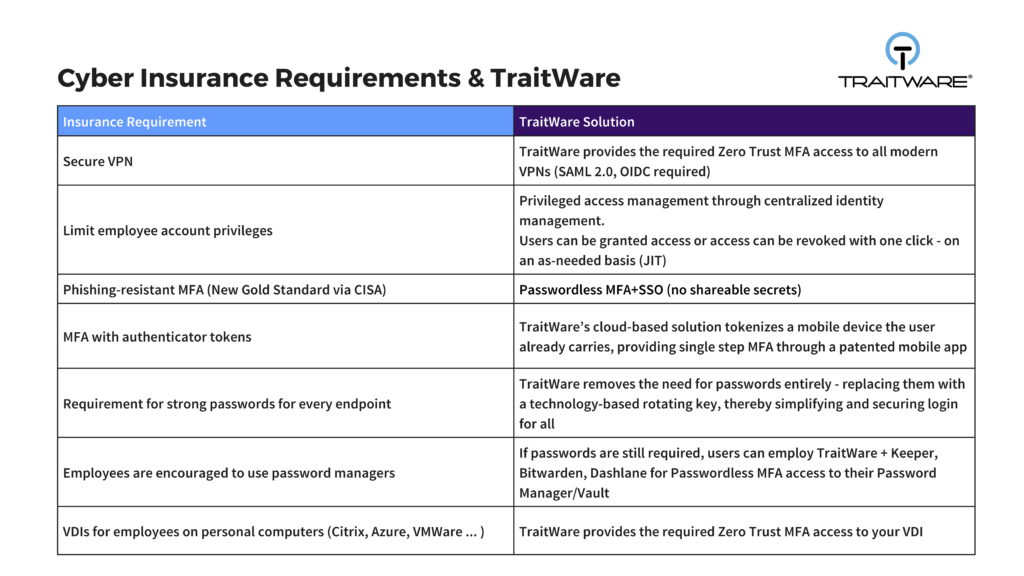
So, before you go spending on insurance, spend a much more palatable sum on putting best security practices in place.
If you’d like to learn more about TraitWare’s Real Passwordless MFA for True Zero Trust Access or have questions about how we can help your company meet today’s security requirements, please contact us at any time.
