WHY SCHOOLS ARE PRIME TARGETS FOR CYBERATTACK, AND HOW WE CAN DO BETTER TO PROTECT THEM
The University of Michigan was in the news recently following a cyberattack that caused an internet outage across all campus networks, eventually requiring password resets for all users. This is just one event amid a series of cyberattacks on schools, and growing concern for the security of the education sector worldwide.
Education is the number one target for ransomware, according to Sophos. Threat intelligence company, Recorded Future, reported that more than 120 schools had ransomware attacks in the first six months of 2023, compared to a total of 188 in 2022. And not only do they struggle to recover from attack – many are forced to shut their doors entirely.
Some examples of shutdowns:
- Highgate Wood School – North London – September 6, 2023
- Nantucket – Four public schools (1700 students) shut down after January 31, 2023 attack
- DesMoines (Iowa) Public Schools cancel classes for 33,000 students – January 23, 2023
- Swansea Public Schools shut down after the January 11, 2023 attack
- Alabama – Jefferson County schools go all-on-paper for two weeks after computer system are shut down post cyberattack – April 11, 2023
- November 16, 2022 – 2 Michigan counties closed their doors
- LA School District computer systems rendered inoperable after an attack in September 2022
- Minnesota – 42 Schools
… and the list goes on
A few more eye-opening facts about cybercrime in schools today:
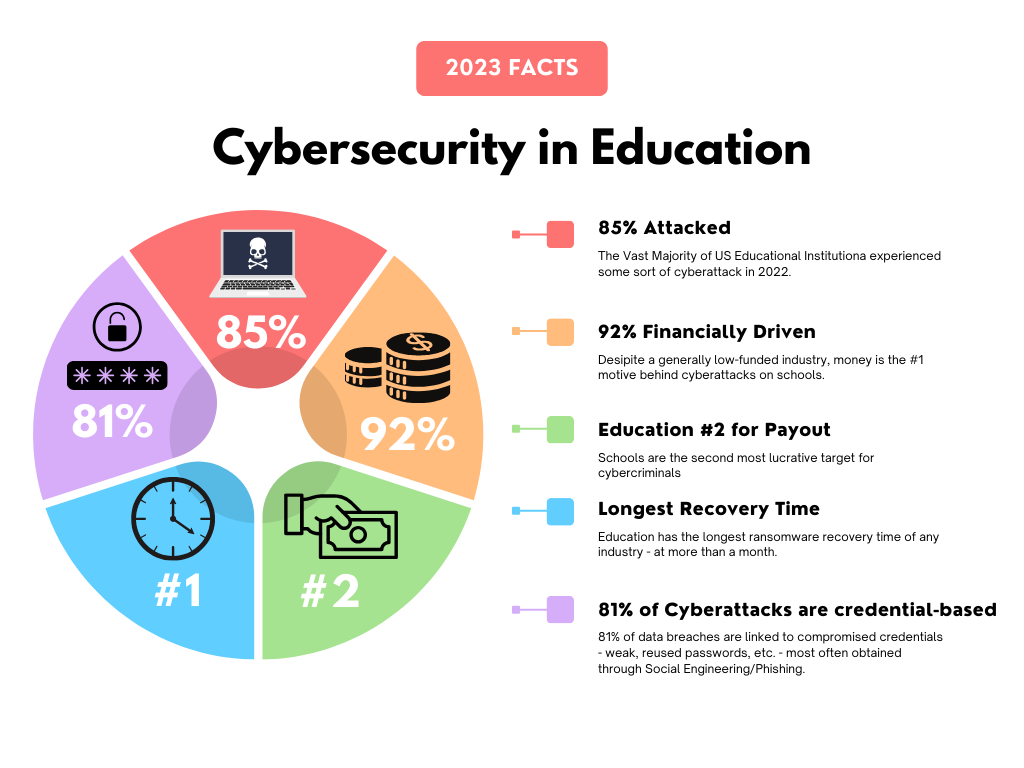
Why are schools prime targets for cybercriminals?
For one, there is a wealth of relatively easily obtained personal information in schools. From passcodes to financials, and potentially on to family members’ info via shared devices and access codes, schools have a lot that criminals want.
Because cybersecurity budgets are generally low in school systems, systems are typically lacking in proper protection, and criminals know it. Experts warn that schools have become easy prey for cybercriminals.
What’s the Primary Motive? Money.
Despite the known lack of budget being allocated to cybersecurity in schools, organizations are primarily driven by financial gain – either selling information to the dark web, using information for fraud, or (#1 method for bad actors) ransomware. Attackers can obtain data and threaten to expose it – unless a ransom is paid.
Unique Challenges for IT in Education
- BYOD (Bring Your Own Device): Students typically use a variety of devices and change them often, and IT needs to secure them. This makes the IT and Help Desk workload significant.
- Remote Learning: Online learning and hybrid models are a part of today’s curriculum, which means devices and locations can be outside IT’s control.
- Remote Teaching: Teachers, especially in higher education, are connecting from various devices to various resources, many of which are also outside of IT sanctions.
- Changing User Identity Landscape: Every semester brings new students and faculty needing to get set up for access and authentication. At the same time, graduates’ accounts need to be closed and/or devices recycled.
- Shared Computing: IT supports and secures shared computers in libraries, common areas, and science, research, or technology labs. This poses clear security challenges.
- Federal Mandates: Higher educational facilities face regulatory pressure to protect students’ applications and personal data. Most call out Multi-Factor Authentication (MFA) as the first measure of security:
- NIST-800-171 requirements to receive government and defense funding grants
- Family Education Rights and Privacy Act (FERPA)
- Gramm Leach Bliley Act (GLBA)
- The Federal Information Security Management Act (FISMA) for institutions receiving federal grants
- HIPAA for protecting medical information
- Reputation is the highest on the list of CISO priorities. Being known for delivering a high-quality, safe, rewarding experience is essential for attracting top faculty, and students (who, one hopes, become top contributing alumni). Reports of compromised personal information, poor security, or ransom payments by schools will negatively impact reputation.
Unfortunately, schools – particularly higher education – have a history of paying high ransoms despite the FBI and others’ advice against it.
The Pushback is Real,
But strong security is now more critical than ever.
With government mandates tightening on cybersecurity for any institution handling sensitive personal information (such as financial), school administrators are urged to make it a priority. …
The BEST News? The most effective tools are simpler to use and more cost-effective than ever.
- Too expensive to implement? … The average cost of a breach (roughly $3.7 million) will be far higher than the cost of implementing strong security.
- Too difficult to effect change across campuses? … Getting every user in the system to reset passwords after an attack can be a massive undertaking, not to mention expensive.
- Too time-consuming? … Schools have the longest post-cyberattack recovery time (more than a month) of all sectors, according to studies. A good MFA solution can be up and running in less than a day.
These are just a few points. But, whatever the reason for doubt, THIS is the season for cybercrime in schools, and schools need to up their game and boost security NOW, or likely suffer grave consequences.
CISO’s Choice – Modern methods for security are better, more affordable, and much easier to use.
The choice between increased risk of attack and putting good security controls in place for education may once have been a difficult one for the CISO, but not only are security controls more readily available now, today’s workforces and students are also much more adaptable to employing new tools.
Resources and guidelines for education and cybersecurity are out there.
Here are a few links:
Protecting Our Future: Partnering to Safeguard K–12 Organizations from Cybersecurity Threats.
Experts Say …
- Backup data
- Regularly install updates
- Employ or begin the move toward a zero-trust security posture. This means making sure all users are who they say they are before they are granted access to digital resources.
- Segment your campus network so the whole system can’t be shut down by one single threat.
- Implement Phishing-Resistant Multi-Factor Authentication (MFA)* to prevent phishing and strengthen verification processes.
- Make it REAL Passwordless Phishing-Resistant MFA by eliminating any knowledge factor – from enrollment to login. *
*It’s important to note the difference between a passwordless experience, where the password is simply obfuscated or hidden, and a Real Passwordless login, where the password has been eliminated – to simplify and secure login.
Anything that has to be typed in, remembered (or forgotten), or that can be shared or guessed, is a security risk you don’t need to take.
Instead, choose a solution that ties the user directly to the login at all times, using biometrics and/or geolocation combined with “something you have” or a device the user already carries. This will not only save on costs and vastly improve security but also make life easier for users and admins.
The Truth About Multi-Factor Authentication / Keeping it Phishing-Resistant
While Multi-Factor Authentication (MFA) is not uncommon, even in schools, it’s important to employ the right form of MFA – both for security reasons and for ease of use.
First, most MFA still uses a password followed by an “OTP” or one-time passcode sent via text, email, or push notification to a device, asking the user to click ‘approve’ to grant access. Unfortunately, the OTP is still a knowledge factor and therefore carries risk. It can be phished, guessed, intercepted, etc. The layer-cake approach is simply not good enough and can be avoided by using a REAL Passwordless method.
For more on the difference between Phishable and Phishing-Resistant Passwordless MFA, take a look here.
Hear it from the Experts – On ReadySetCyber

As we move into this school year, cybercrime is a top concern. Whether you’re in IT, a professor, a student, a staff member, or a parent, your choices around cybersecurity could be hugely impactful for many.
On this month’s edition of ReadySetCyber, we’ll tackle the issues surrounding cybersecurity and our educational systems with a panel that includes IT decision-makers in our academic institutions, educators, experts, and service providers. We’ll tackle the issues, take questions LIVE from the audience, and engage in lively unscripted discussion.
On the Roster:
Darren Mott – HOST – FBI Special Agent (Ret.)
Randall Trzeciak – Carnegie Mellon
Kevin Powers – Boston College
Evan Rice – GuideStar
Heath Spencer – TraitWare
Hope to see you there!
Any questions, we’re always happy to chat
