How TraitWare® Can Secure and Simplify the Healthcare Industry
Updated June 2019
“Secure and Simplify Your Digital Life.”™
Summary
TraitWare® cutting edge security technology eliminates usernames and passwords to protect electronic protected health information (EPHI). TraitWare® can help healthcare customers with compliance, user experience, and overall security. We strive to meet, and when possible, exceed the authentication recommendations and guidance provided by HIPPA, CMS, and NIST. We use passwordless authentication with inherent multifactor authentication to secure your data while reducing user friction around logging into websites. Issued and filed patents cover the proprietary processes that achieve these standards of security and simplicity.
Overview of HIPPA Authentication Standards
When Title II of the Health Insurance Portability and Accountability Act (HIPPA) was established in 1996, the Internet was still in its infancy. This Act was passed with the best intentions in order to protect the privacy of every American as it related to their individually identifiable health information. Privacy was as important then as it is now, but the means to invade, steal, and use personal information to crippling effect has continued to grow over time. Twenty years later we are in the midst of a more mature digital world that reaches far beyond the Internet into nearly every facet of our daily lives. Due to this inescapable reach, it has become increasingly necessary to safeguard the one thing that is most dear to us, our identities.
Standards and safeguards have continued to evolve and the Federal Government has continued to provide guidance and regulations to persuade the healthcare industry to stay vigilant with respect to best practices in securing our Protected Health Information (PHI). Putting even more pressure on the industry, the HITECH Act became effective on Nov 30, 2009, which increased the penalties for HIPPA rules violations up to $1.5 million.
One of the largest threats to privacy as health records move into the electronic realm is the lack of means to ensure they are accessed only by those who are authorized. The security breaches at Sony-Pictures, Anthem, Target and others show that even large multi-national corporations are susceptible to massive digital attacks when systems continue to rely on the combination of usernames and passwords. This long-standing industry standard has become a security pariah and has been directly responsible for the loss of data from some of the most recent and high-profile hacks; more recently, even multi-factor platforms that still depend on usernames and passwords have been breached.[1]
A Reuters article reported that “your medical information is worth ten times more than your credit card number on the black market.”[2] This alone is a startling fact. Couple that with the mind of a profit-seeking, disruption-motivated hacker group and you can be sure the threat is persistent and real. In fact, the hackers are probably ahead of the industry as only a few of our health records are available via patient or provider portals. Most of these portals are protected by a username and password. The hackers continue to attack and the healthcare world’s electronic records are a large target.
TraitWare® is dedicated to Secure and Simplify your Digital LifeTM by eliminating the need for usernames and passwords. When it comes to the healthcare industry, we are excited to offer solutions that keep our customers in compliance with the latest HIPPA authentication requirements and recommendations while offering vastly improved security. In an interview with Jeremy Grant, Senior Executive at the National Institute of Standards and Technology (NIST) and former head of the government’s National Strategy for Trusted Identities in Cyberspace (NSTIC), he spoke to the goal of completely eliminating the use of usernames and passwords for authentication. Jeremy stated that he is “optimistic that we’re nearing a tipping point right now with the new types of technologies that are emerging.”[3] With the latest developments provided by TraitWare®, that goal has been reached. We are excited to help all of our customers replace their usernames and passwords to significantly reduce or eliminate their potential exposure to security breaches and subsequent fines.
Now is the Time to Finally Replace Usernames and Passwords
The HIPPA Security Rule defines Technical Safeguards in §164.304 as “the technology and the policy and procedures for its use that protect electronic health information and control access to it.” These policies and procedures allow covered entities to “use any security measures that allow it reasonably and appropriately to implement the standards and implementation specifications.”[4] More specific to authentication standards, §164.312(d) states that covered entities should “implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.” The Centers for Medicare and Medicaid Services (CMS), who are tasked with enforcing the HIPPA Security Standards, report that the majority of healthcare related authentications are performed using passwords.3 This is unfortunate and potentially disastrous. According to the 2017 annual Data Breach Investigations Report compiled by Verizon, 81% of hacking data breaches could be traced back to some stolen and/or weak passwords.[5] The 2018 Verizon data summary shows that data breaches in the healthcare industry are increasing, with human error being a major factor.[6]
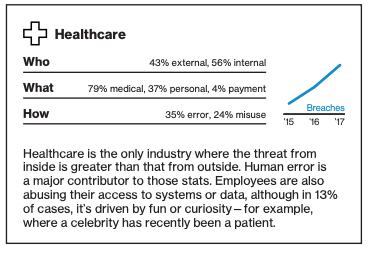
While the HIPPA technology standard[7] on authentication of a person or entity has no implementation specification, it does require covered entities to “implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.”
Passwords do not truly meet the standard of verifying that the person accessing EPHI is the correct person. TraitWare’s® patented and patent-pending technology is ready to help our customers make the switch to a world without passwords and keep several steps ahead of those wishing to compromise PHI, while at the same time increasing the simplicity of logging in for the user and ensuring the person accessing protected health information is the one claimed. Eliminating passwords stops the sharing of passwords and misuse of others’ accounts by employees and co-workers. It also stops the use of stolen passwords and the ability to “stuff” passwords, whether stolen or fabricated.
The relevant federal regulations for the protection of personal health information are in 45 CFR 164.312 (d) – eCFR. These regulations, current as of March 19, 2019, were reviewed for this update.
How TraitWare® Can Meet Your Authentication Needs
We realize that EPHI can be accessed in a variety of ways from a variety of locations. Specifically related to mitigating risk for lost or stolen login/password information for remote access to EPHI, the CMS has recommended implementing two-factor authentication.[8] CMs now requires MFA for certain records.[9] Two-factor authentication uses a combination of factors to help prove your identity during a login. These factors are ‘something you know,’ like a password or PIN, ‘something you have’ such as a smartphone, and ‘something you are,’ which refers to a biometric like a fingerprint. From internal private networks to consumer web portals, TraitWare® is a platform that supports the numerous avenues our customers and their user base use to access EPHI.
Many are familiar with the one-time passcode (OTP) method of two-factor authentication. A user attempts to log in with a username and password and a short numerical passcode is sent to your phone in a text message. You enter the passcode into the prompt and you are logged in. While that is one method of two-factor authentication, there are still security risks and the user experience is error prone and cumbersome.
TraitWare® is an authentication solution that eliminates usernames and passwords and simplifies the user experience, while providing the additional security needed to prevent data compromise and loss. We do this by using your smartphone for the entirety of the login and authentication process. A person with a registered TraitWare® app on their smartphone only needs to authenticate the app using a biometric (facial or fingerprint) or visual PIN, which we call PhotoAuth®. Once authenticated, the person can log into a PC website by scanning a QR code on the PC screen using the app, or the site can be automatically opened on their TraitWare® registered mobile device. Behind the scenes TraitWare® is handling all of the security and authentication to instantly and seamlessly log in a user without a username or password.
There are many actions that take place behind the scenes to verify the identity of the user that are unique to the TraitWare® process. All of these pieces work in tandem and are seamless and nearly invisible to the user.
User Authentication
From the user perspective, they need to perform only one action to authenticate their smartphone for use in logging in without a username or password. This is either using a fingerprint reader or facial reader on the smartphone (such as those using iOS or Android operating systems) or entering a PhotoAuth® sequence of 5 pictures from a unique set of 24 pictures on their device, which is a visual PIN. Once this is done, the device releases a unique key that represents a correctly used biometric or valid PhotoAuth® sequence from a trusted smartphone. This key is sent to the TraitWare® server for verification and does not contain any biometric information. This represents “something you are” (fingerprint or face) or “something you know” (PhotoAuth® sequence).
Device Fingerprinting
When a person first registers the TraitWare® app after an initial identity proofing process decided by each customer, we take a digital fingerprint of the user-created content on the device on which the app is installed. This content is comprised of items such as contacts, music, and the list of user-installed apps. That digital biometric is mathematically converted to prevent any possible recovery of personal information. Based upon the device fingerprint comparison, using TraitWare’s® patent-pending specially designed algorithm, we are able to confirm it is a unique device to that user, with odds of 1 in 360 billion. The digital biometric is sent encrypted in a packet sign with a private key unique to the user. On subsequent authentication attempts, TraitWare® executes an updated device fingerprint for comparison. Even when a person substantially changes the content on their device, the TraitWare® algorithm is able to confirm it is the same user. This represents a highly unique and completely confidential combination of “something you have” (your smartphone) and “something you are” (your unique digital biometric).
Cryptographic Safeguards
We create a unique public/private cryptographic key pair that we use to digitally sign communications to our authentication server. Once the public key is registered with our server during the initial app activation, each authentication attempt is digitally signed by the private key, proving possession of the device. This helps to prevent man-in-the-middle type attacks and allows the TraitWare® authentication server to verify the integrity of the data it receives from the user’s smartphone during an authentication attempt. In addition to data integrity, possession of the correct cryptographic keys represents ‘something you have’ (your smartphone).
TraitWare®Authentication Server
After the user has authenticated their smartphone, they are able to use it to log into protected sites, such as those with EPHI. On a PC login screen used to access EHPI, instead of a username or password, the user is presented with a QR code unique to your system, which confirms to the user that they are working with your server and not one that has been spoofed. They scan the QR code with their authenticated TraitWare® smartphone app to login. For logging in on a mobile device, users can either select a site from a list of allowed websites within the app or navigate directly to a mobile site to login. Each of these login methods set off a behind-the-scenes sequence of steps that are based on the OIDC , SAML and OAuth 2.0 authorization protocols.[10] The server containing the EPHI communicates directly through an encrypted channel with the TraitWare® Authentication Server. If the user has been successfully authenticated, the TraitWare® server passes an authentication token to the EHPI server, which is then able to grant access to the user. This happens instantaneously and is hardly perceptible to the user, creating a seamless and secure login experience without usernames or passwords. You are assured it is the correct user and their smartphone attempting to gain access and they are certain the server they are accessing is yours.
TraitWare® also has the ability to use location awareness to help make authentication decisions. Each time a person attempts to authenticate the TraitWare® app on their smartphone, the TraitWare® Server can check to verify that the person’s smartphone is in a location that has been pre-approved for access. For example, a person may be given permission to access protected information from both a work and home location, but not anywhere else. This helps prevent unauthorized access attempts from stolen or cloned devices and discourages users from accessing sensitive information in unsecured environments.
There are a variety of options for different needs, and TraitWare® offers solutions for both remote access login authentication as well as internal network authentication. The TraitWare® platform by design is ready to provide IAL3 and AAL2 for e-authentications as defined in NIST SP 800-63-3[11] to meet Federal authentication guidelines. (See TraitWare NIST 800-63-3 Compliance, October 2018.[12])
Consider the TraitWare® solution to eliminate usernames and passwords from your workflows forever, and let us help you Secure and Simplify your Digital Life.TM
[1] https://www.securityweek.com/hackers-bypass-mfa-cloud-accounts-imap-protocol
[2]http://www.reuters.com/article/2014/09/24/us-cybersecurity-hospitals-idUSKCN0HJ21I20140924
[3] http://www.bankinfosecurity.com/interviews/slow-path-to-password-replacement-i-2467
[4]https://www.hhs.gov/hipaa/for-professionals/security/index.html
[5] http://www.verizonenterprise.com/DBIR/2019/reports/rp_dbir-2019-executive-summary_en_xg.pdf
[6] https://enterprise.verizon.com/resources/reports/DBIR_2018_Report_execsummary.pdf
[7] https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/administrative/securityrule/techsafeguards.pdf?language=es
[8]https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/administrative/securityrule/remoteuse.pdf?language=es
[9]https://www.cms.gov/Medicare/Coordination-of-Benefits-and-Recovery/Coordination-of-Benefits-and-Recovery-Overview/MSPRP/Medicare-Secondary-Payer-Recovery-Portal.html
[10] https://www.traitware.com
[11] https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63-3.pdf