In recent months, the notorious Scattered Spider cyberattacks have made headlines with high-profile breaches targeting major organizations. These attacks are not only sophisticated, but also a stark reminder of a dangerous truth: any login system that relies on shareable secrets is fundamentally vulnerable.
What Is Scattered Spider and How Do They Attack?
The Scattered Spider cybercriminal group specializes in social engineering attacks and other tactics designed to trick employees into revealing login credentials or multi-factor authentication (MFA) codes. Their techniques include:
- Phishing and impersonation: Pretending to be IT staff to steal passwords or MFA tokens via phone, SMS, or email.
- SIM swapping: Hijacking mobile numbers to intercept texted authentication codes.
- Push bombing / MFA fatigue attacks: Repeated login requests until a user accepts one.
- Help desk manipulation: Convincing support teams to reset passwords or MFA devices.
The common thread? These attacks all depend on capturing or intercepting shareable secrets – information that can be passed from one person to another.
The Problem With Shareable Secrets
A shareable secret is any piece of information a user knows or receives that can be used to log in. This includes passwords, one-time passcodes (OTPs), and answers to security questions.
Once an attacker has a shareable secret, they can:
- Bypass MFA systems
- Hijack user accounts
- Register their own MFA tokens
- Escalate privileges for deeper access
- Steal data and deploy ransomware
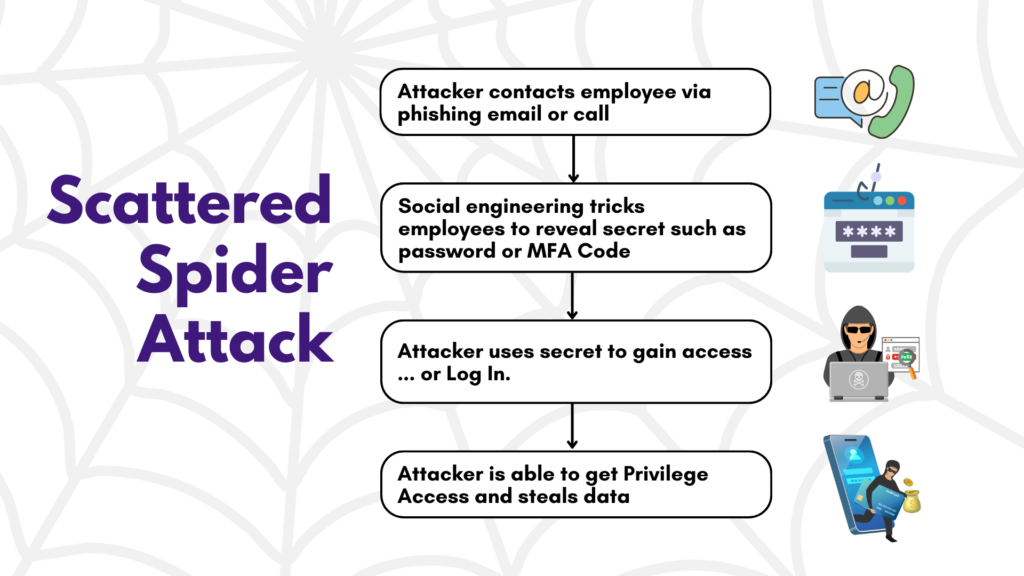
Scattered Spider has shown that even advanced MFA solutions are not immune if they rely on these vulnerable secrets.
Zero Shareable Secrets: The Passwordless Solution
The best defense against cyberattacks like Scattered Spider is to eliminate shareable secrets entirely from the authentication process.
TraitWare offers passwordless, phishing-resistant MFA that removes passwords, usernames, and codes from the login flow — eliminating the single most exploited weakness in modern authentication.
How TraitWare Works:
- Device possession: Authentication is tied to a registered device.
- On-device biometrics: Face or fingerprint recognition verifies the user.
- Behavioral patterns and geolocation: Optional geofencing adds location-based security.
- Visual PIN: Optional, never leaves the device.
All authentication happens locally on the device, meaning there is nothing to phish, nothing to intercept, and nothing to trick a help desk into revealing.
Why Passwordless Simplicity Matters
Complex login processes frustrate users and drive them to risky workarounds. TraitWare’s Zero Shareable Secrets approach makes security simple and seamless, with one mobile app securing both local device logins and cloud applications through industry standards like SAML and OIDC.
The Takeaway for Scattered Spider-Style Threats
As long as organizations rely on passwords and OTPs, cybercriminals will have an entry point. With Zero Shareable Secrets, that door is closed.
TraitWare provides “phish-proof,” replay-resistant, and passwordless authentication from onboarding to recovery – exactly the level of resilience needed to combat attacks like those from Scattered Spider.
If you want your business to stay ahead of evolving cyberthreats, it’s time to leave shareable secrets behind.
Learn more about TraitWare’s Zero Shareable Secrets approach → Contact us any time for your free trial or personalized demo.
