Up To 5-Factor Authentication
TraitWare® Eliminates Usernames + Passwords With Frictionless Secure Multi-factor
Device

Something Only you have
PhotoAuth™

Something Only you know
Biometric

Something Only you are
![C:\Users\owner\AppData\Local\Microsoft\Windows\INetCache\IE\5SBKJPEU\Equal[1].png](https://traitware.com/wp-content/uploads/2020/03/eq.png)
Secure Lock

Creating a Secure Lock
The Base Factor
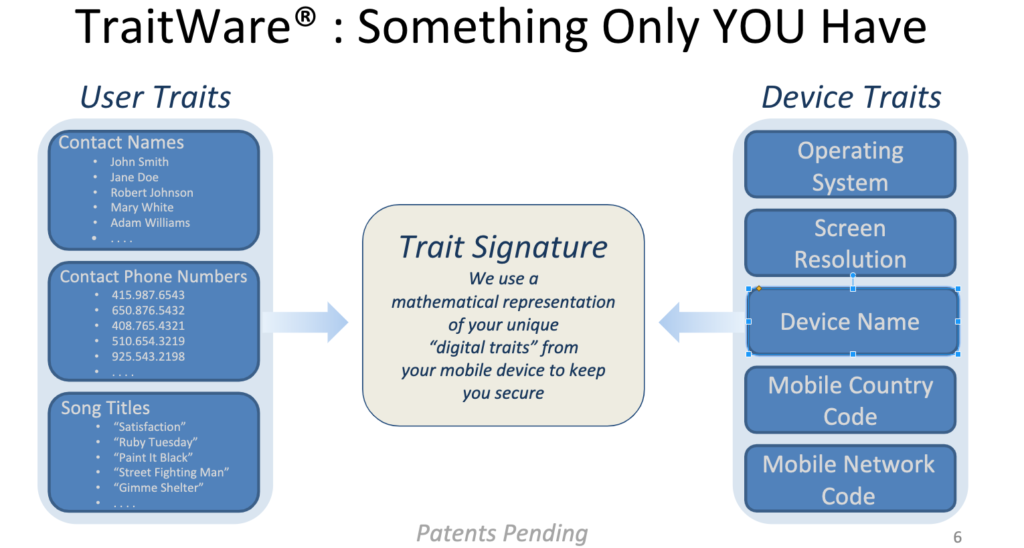
The base of the TraitWare multi-factor solution is the possession of a device that is unique to an individual.
The TraitWare solution is developed from the concept that each individual is unique and that as we use our device, it becomes unique to the individual. For example, we select different apps to use on our device; we add contacts, including names, phone numbers, and addresses. We add photos and music, select different colors and backgrounds, name our devices, and use apps and programs that store data on the device. All of these make the device unique.
TraitWare performed studies demonstrating that several of these items can be captured and compared against the same list of items on another individual’s device, and even if the user deletes or adds 40% of the content, the device statistically can be differentiated from devices owned by another individual to 1 in 300 billion. In addition, as you continue to use the device, data is stored on it, most of which is transparent to the user.
For example, TraitWare stores a set of photos for use in creating a knowledge factor. The pictures are a random set from a larger set, creating another unique feature. TraitWare also creates a public and private key set for digitally signing information sent from your device. Using the unique features that we call Traits and storing them hashed (obscured) on the TraitWare Authentication Server allows TraitWare to determine that the request for authentication is coming from your registered device. The information is gathered each time the TraitWare app is opened and transmits and compares on the authentication. The data is obscured for your privacy while still retaining its unique qualities. For the authentication to proceed, your device has to be verified as a registered device.
TraitWare recommends the use of a smartphone as the security token that an individual possesses. We also allow the use of tablets. The phone is a preferred device because you tend to keep it within three feet of yourself and have physical control of the device the majority of day and night.
Achieving 2-Factor Authentication
To the possession of a unique device, TraitWare adds a factor – something you are or something you know. For something you are, TraitWare uses either a fingerprint registered to your device or a facial image registered to your device. For iPhones, Apple has reported the fingerprint is unique to 1 in 50 thousand and the face is unique to 1 in 1 million. iPhone facial recognition would require the construction of a 3D model of a user’s face in order to spoof the system. The security of fingerprint and facial recognition in Android devices varies according to the manufacturer.
For the factor “something you know,” TraitWare uses the selection of five images out of 24 images. The images that are used are a random set from a larger set of images. Making the set unique to your device, for use with multiple accounts, the same set of pictures is available for setting up the knowledge factor. The user can select the same set or a different set for each account. The selection of five images out of 24 meets current NIST Level 2 security standards. For more information on PhotoAuth™, click this link to a white paper. Note: the account holder can require that the set of 24 images be randomly displayed to prevent to use of a pattern and to make shoulder surfing more difficult.
Achieving 3-Factor Authentication
In the TraitWare system, three-factor can be achieved in any of four ways:
a. require possession, a biometric and knowledge factor;
b. require possession and two knowledge factors;
c. require possession, a knowledge factor, and location;
d. require possession, a biometric and location.
In the 3-factor authentication mode, which is set from the control console by the account holder, the authentication will revert to using the possession, PhotoAuth™, and the device pin if the biometric fails to authenticate.
Achieving 4-Factor Authentication
Four-factor authentication is achieved by requiring possession, location, a biometric, and a knowledge factor or, by requiring location, a biometric, and two knowledge factors.
The TraitWare location requirement is set up in the Authentication Control Console for each user within an account. When the location requirement is on, authentication is only granted from locations that have been pre-approved. Multiple locations of various sizes can be pre-approved.