And How MSPs Can Reduce Risk
In a joint advisory issued this May, several International government agencies — the Cybersecurity and Infrastructure Security Agency (CISA), the UK’s National Cyber Security Centre (NCSC-UK), the Australian Cyber Security Centre (ACSC), Canadian Centre for Cyber Security (CCCS), New Zealand National Cyber Security Centre (NZ NCSC), US National Security Agency (NSA), and the FBI — warned that MSPs are increasingly at risk of attack. They outlined steps to take now to bolster security. (Read Full Report Here)
MSPs are particularly attractive to cybercriminals
Why MSPs are at risk of attack:
a. because of the value of the information they are accessing remotely from their customers
b. because obtaining access to one MSP likely means access to a host of information that the MSP has access to. Financial info, security, and so on. The potential for follow-on malicious activity across an entire MSP customer base is serious.
One example of the potential consequence is the REvil ransomware attack on Kaseya, the MSP software provider. The breach spread to dozens of MSPs and over 1,500 of their customers. This illustrates just how fast an attack spiral out of control.
But why are we bringing this up months later?
Because the threat landscape has evolved … and SO SHOULD WE
Many MSPs have good defenses in place, but the attraction and potential payout from one attack appear to outweigh the obstacles for attackers. And one attack could be crippling for an MSP – both financially and in terms of reputation.
What can MSPs do now to better protect themselves and their customers?
The Federal agencies listed above issued lengthy guidelines for security measures that MSPs should take. Hardening devices and internet-facing services, along with internal security and account controls, to name a few. Most of the message encourages companies to apply common sense and good cyber hygiene, but the guidelines are worth reading through.
The guidance is also good for customers assessing an MSP’s security controls. NOT having the essentials in place, in other words, could mean a loss of business.
Here are the highlights:
- Set up multi-factor authentication (MFA) everywhere possible **
- Back up your systems to prevent loss and potentially even ransom
- Update / Patch software regularly
- Segregate networks internally and across customer networks to prevent spread and isolate affected systems in the event of attack. NEVER reuse passwords!
- Use a Zero Trust framework to ensure that privilege and access are granted only as users need it to do their job. This means deactivating unused accounts.
- Train staff so that they know best practices and warning signs of attack
- Have an incident response plan in place just in case an attack occurs. Encourage your clients to do the same, knowing that the time it takes to set up will be FAR LESS than recovery from an attack.
- Determine the risk – If you have lots of SaaS, for example, you’ll likely not know exactly which apps are protected and which are not. (READ MORE on Detecting Unprotected SaaS)
** WHAT’S MORE
#1 on the list of recommendations: Set up and enforce Multi-Factor Authentication (MFA)
“Organizations should secure remote access applications and enforce MFA where possible to harden the infrastructure that enables access to networks and systems,” notes the report.
For us, MFA is critical for any type of cyber defense. But we’re going to take it a step further.
Just Any MFA is JUST Not Good Enough.
Yes, MFA is great because it complicates things for bad actors, setting up an added obstacle to overcome. But, as we’ve seen with recent attacks, some MFA can be bypassed through sophisticated methods and with tools that are making that bypass easier and easier to carry out.
“[Russian state-sponsored hackers] have recently demonstrated the ability to exploit default MFA protocols; organizations should review configuration policies to protect against ‘fail open’ and re-enrollment scenarios,” the report says.
But it’s not just Russian hackers gaining access to our company valuables. Traditional or “Legacy” MFA is being bypassed by attackers from anywhere.
A recent example is the TWILIO attack, which affected their customers, Authy users, and eventually Okta. In this phishing campaign, the hackers accessed 93 Authy user accounts. The hackers were then able to register their own mobile devices on the compromised accounts and intercept the Authy 2FA codes. … This is just one instance that points to the unreliability of SMS-based 2FA.
In other words, it must be NON-Phishable MFA.
What is Non-Phishable? Simply put, any of the multiple factors used to authenticate a user must not be factors you need to remember or type in … or any shareable secret. This includes email or SMS notifications, PIN codes, security questions, etc. To illustrate, we’ve put together the following chart.
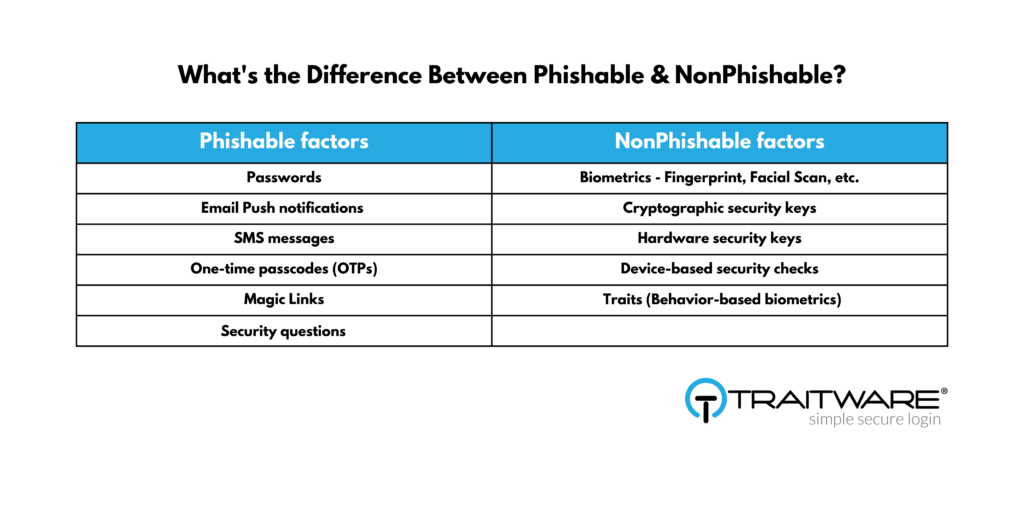
TraitWare provides Passwordless MFA + SSO for Zero Trust access. This means we’ve eliminated the need for the password, which is the #1 phishable threat vector behind cyber-attacks. Otherwise put, none of the factors we allow for authentication are phishable, making it not only more secure but easier to use.
If you’re interested in learning more about how TraitWare works with MSPs, or how we can get you and your customers set up quickly and easily with Passwordless MFA + SSO, please contact us at any time.
