And why you should use Strong MFA instead
Despite the call from world leaders for strong Multi-Factor Authentication (MFA) to protect individuals and organizations against cyber-attack, the vast majority just isn’t up to snuff when it comes to security.
Most of us know that security starts with Identity and Authentication – ensuring that users Are Who They Say They Are before they’re granted access to company resources and digital valuables.
One of the questions we get often is, “How is your solution – or any strong MFA solution – different from a free authenticator app.? … Isn’t all authentication essentially doing the same thing?”
The short answer is No. Not all authentication is doing the same thing, and the differences are many. The Gist?
Most authenticator apps are using 2FA – typically a One-Time Passcode (OTP) or push notification on top of a password for access. The problem is that all those factors are ‘Phishable’ – or often easily accessible by an attacker. Why? Because they are typed, remembered, and/or shareable (something you know or a ‘knowledge factor’) which means bad actors can use various methods to obtain them. Guessing, social engineering, MFA fatigue, push attack, etc. are among the common and increasingly easy methods used by attackers.
Arguably, 2FA is not much better than a password alone. Why? Because free authenticator apps will likely fall back on that password or unsecured or ‘Phishable’ factor for authentication.
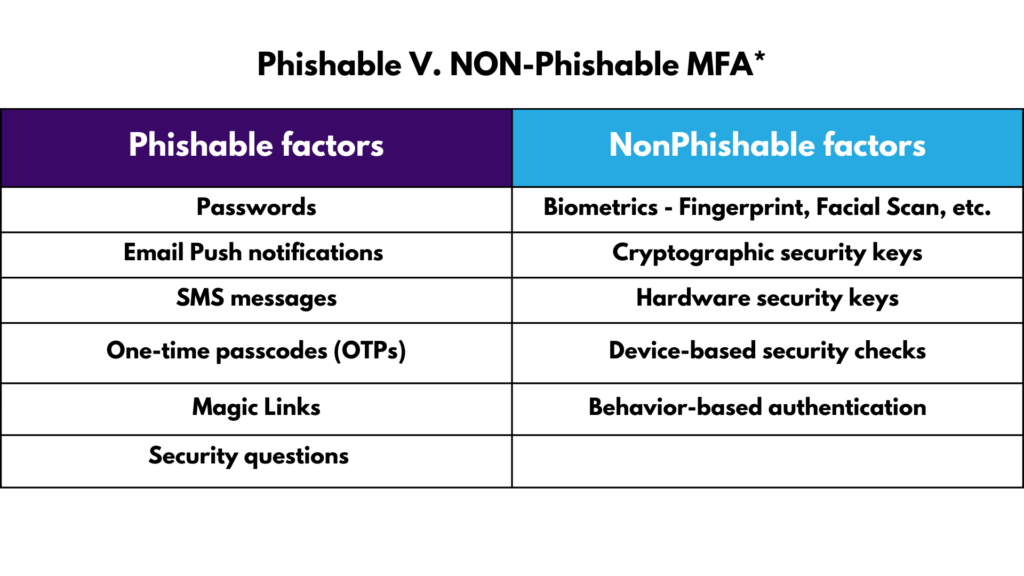
What’s Phishable and What’s Not?
And Now, 7 Reasons you shouldn’t use authenticator apps for login security
1. Physical access and people looking over your shoulder
Someone might look over your shoulder when you’re using an authenticator app and see the one-time code. And maybe not just one code, as authenticators often display several codes in a row, which could allow the attacker to log in to any of those accounts.
Worse, if someone got their hands on an unlocked smartphone with an authenticator, they could gain access to all your accounts without much difficulty.
2. Phishing sites
While most phishing sites are set up primarily to harvest usernames and passwords to sell on the dark web, and 2FA can help protect against these kinds of attacks, cybercrime is rapidly advancing, and sophisticated methods are more accessible to cybercriminals and more common.
In many cases, attackers can imitate the two-factor authentication mechanism, and not only intercept the login and password but also the one-time code. They can then log into the victim’s real account.
Phishing is the #1 attack method for cybercrime and it can be difficult to protect against it.
3. Stealing malware
One critical truth is that services aren’t keen to lose customers because of friction, or because of the loss of an authenticator. So, they usually provide an alternative login method such as sending a one-time code or confirmation link to the owner’s email address.
This means that if a leak occurs and attackers have the password and email address, a bypass attack is not only possible, it’s likely. … 2FA then essentially becomes no more secure than a password for access.
What happens then?
After you’re successfully logged in, the service saves a small cookie on your computer, which contains a secret number. This file is what your browser will present to the service for authentication from that point on. So, if someone manages to steal this file, it can be used to sign into your account. No password or one-time code will be necessary.
These files (along with a host of other information like browser-saved passwords, cryptocurrency wallet keys, etc.) can be stolen by Trojan Stealers. With a Stealer on your computer, you’re at serious risk of other accounts being taken over as well.
In fact, experts say that most mobile authentication apps can be breached by malware.
Most authentication apps use cryptographic keys which generate the codes used to identify users. If these keys are stolen, they give a bad actor the ability to authenticate transactions or sign documents on a user’s behalf. This is why most authentication apps try to make use of the safest storage available for these keys.
For many developers, this means a mobile phone’s Trusted Execution Environment. In Android phones, this is known as the StrongBox Keystore. In Apple, this is the iOS Secure Enclave (which has a companion software called Keychain that stores encrypted data such as passwords).
V-Key CTO Er Chiang Kai points to a flaw in the architectural design of these apps – called the ‘Trust Gap’, “which hackers can exploit using malware to illegally obtain a target’s authenticator keys. This enables bad actors to make unauthorized transactions or sign bogus documents, opening up a digital service to account takeovers, data leakage, fraud, or worse. This is an insidious and sophisticated attack as the targeted authentication app doesn’t even need to be running or be tampered with to be compromised.”
4. Lack of authenticator backups
If you somehow lose your authenticator, access to your accounts can also be lost – even permanently. This can happen if your phone breaks to the point that data is no longer retrievable or if your phone is lost or stolen.
- In the event that your authenticator can’t back up data properly (which is often the case) you’ll need to install the authenticator on more than one device, or even use several apps to ensure recovery.
5. Compliance Requirements:
Many regulatory standards, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR) require MFA to be implemented in order to protect sensitive information. Most authenticator apps won’t meet these requirements.
6. Flexibility:
Most strong MFA solutions can be customized to meet specific security needs. This includes the ability to employ different authentication factors such as biometrics, tokens, and/or mobile devices. Authenticator apps are generally limited in their flexibility.
7. Ongoing Support:
A good MFA solution includes ongoing support and regular updates so that the solution remains effective against emerging security threats.
What’s the Solution?
- We recommend companies use Strong MFA that is non-phishable or Phishing-Resistant (as the above table outlines). Non-phishable factors include factors that tie login to the user. and are typically not available as factors for authentication on free authenticator apps.
- Make sure the solution is compatible with the systems you’re running. Google Authenticator, for example, works with other Google products but not for others.
- Make sure the solution allows for Single Sign-On (SSO) so you can access all your applications from a single console. Most authenticator apps don’t allow for this.
- The Bottom Line = YOUR Bottom Line. … Deploying simple secure Passwordless MFA + SSO should be affordable but also save on costs.
In summary, there are too many situations where the free authenticator apps using 2FA are vulnerable and will potentially result in devastatingly costly results.
If you have questions about how TraitWare’s ‘Phish-Proof’ Passwordless MFA+SSO works to eliminate the highest risk factors, friction, and complication, please get in touch.
We’re here to help!
But, Seeing is believing. Don’t take our word for it. Read what our happy customers have to say.
