It’s Time to Fix What’s Been Broken From the Get-Go
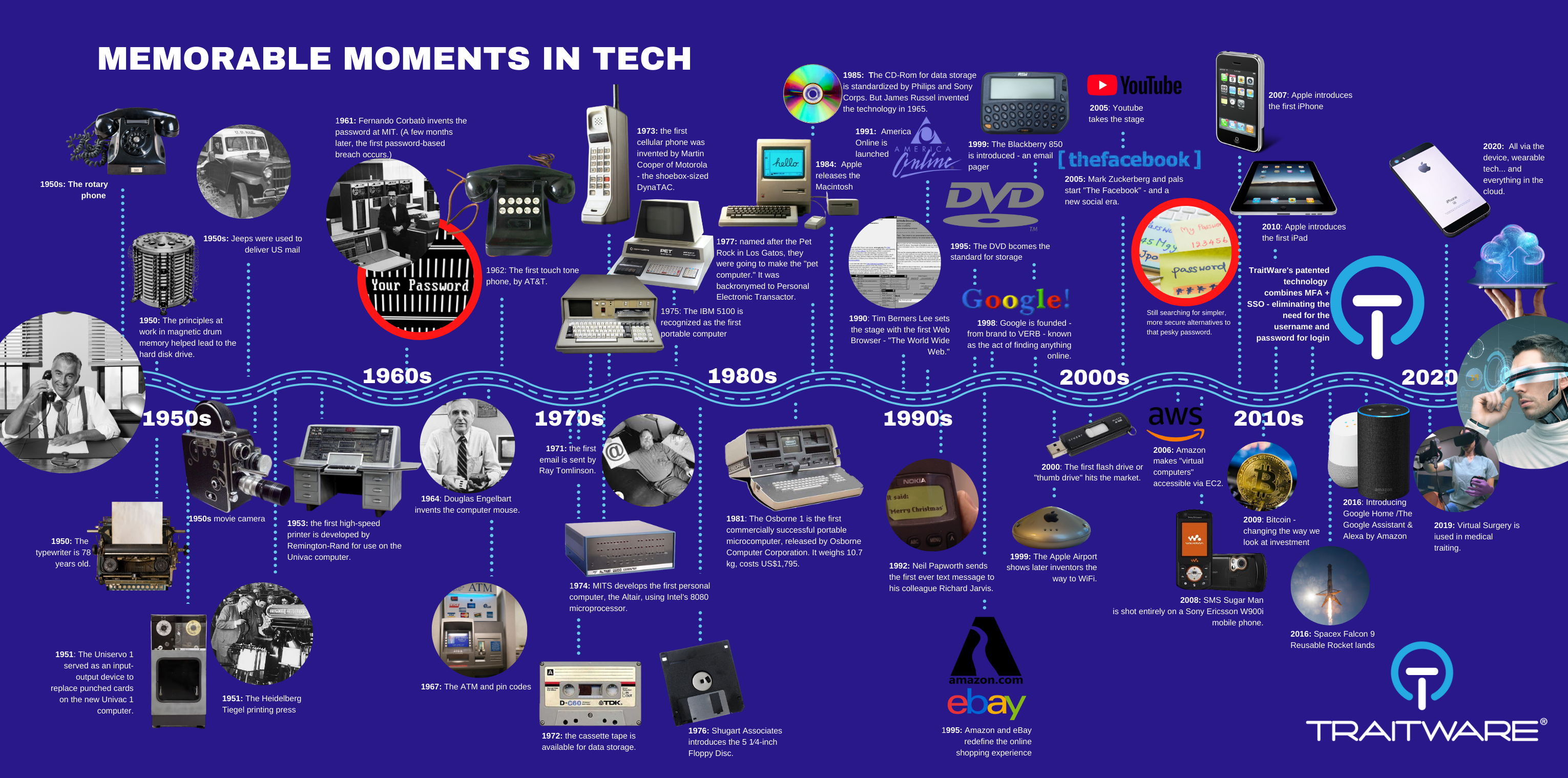
As humans, we’ve evolved a fair amount. But Technology is another animal altogether. Taking a look at our infographic, the technological shifts we’ve witnessed since the 1950s are nothing short of mind-blowing. From pen and paper and a phone to today’s superpowered mobile devices, AI, and cloud-based everything, our world seems to have gone from ‘physical’ to ‘digital’ in the blink of an eye.
And, the rate of change, since Tech became a thing back some 70 years ago, is crazily exponential. I can still remember a time when the thought of having a personal computer to produce documents for school or work was UNHEARD OF. Fast forward just 30 years to today, and our mobile devices are practically appendages. After-school get-togethers with friends to play kickball and hide-and-go-seek have been replaced by chat rooms, online games, and constant surfing of the web. Telephone calls and letters to friends have been replaced by texts – this kind of shorthand code our young ones tap out with their thumbs at ridiculous speeds – ttyl, brb, lol, np, and on and on. … Devices are everything – from Bauble to Best Bud to Babysitter. This is progress.
Except for the Password. The awkward, incredibly insecure, easily forgotten or stolen, ubiquitous Password continues to hold us captive.
Passwords are bad. Everyone knows it. Everyone hates them (except for hackers and identity thieves). They’re messy, frustrating, and the systems that keep them working are old, clunky, and expensive to maintain. What’s worse is that people tend to use the same credentials across multiple applications, making the threat of cyberattack even more severe. Once in the wrong hands, those old character strings can be used to impersonate us everywhere – and from that, it is difficult to recover. Even Bill Gates declared the password “dead” at Microsoft’s annual IT Forum in Copenhagen in 2004!
In fact, the password, invented in 1961 at MIT by Fernando Corbató, has always been a bit broken. It wasn’t really designed to handle the Umpteen applications and accounts we need access to today. Stored in plain text, they were pretty easy to hack. Just a couple months after its invention, one MIT PHD student, Allan Scherr, wanted to bump up his usage time on the computer they all shared – The Compatible Time-Sharing System (CTSS) – so he submitted a punched card with the account number and file name with a request to print all password files. The next day, they were all there, and Scherr was able to get more machine time. He was never caught – but, decades later, proudly admitted to his scheme.
Today we have hashing, sure, but the password remains the most vulnerable and inefficient means for access security out there. Corbató himself, who died a year ago at 93, told the Wall Street Journal in 2014 that he kept dozens of his passwords on three typed pages. He called the current state of password security “kind of a nightmare.”
Why is it then that this one pesky little thing remains frozen in time?
We do have biometrics – facial recognition, eye scanning, fingerprints … but most systems that use multi factor authentication (MFA) are simply layered on top of the old username and password. And those credentials we keep on post-its and saved in our browsers, are the number one threat behind data breaches – costing companies upwards of 5 trillion dollars each year. It’s estimated that one password reset will cost a company an average of $70.
There is a better way to secure and simplify access, and save on costs for your company.
Let’s take a look at some of the perceived challenges companies face, or arguments against ditching the username and password method – and how we can address them with modern technology.
Perceived Challenge 1:
Biometrics aren’t available on every device.
Biometrics, such as fingerprint scanning and facial recognition, have become more widely used, but aren’t available on every device, especially older mobile phones, laptops, and desktop workstations. Companies have been reluctant to adopt this technology for this reason.
Facts:
91% of college grads have a smartphone or mobile device. 81% of Americans own a smartphone. And, most smartphones allow users to open their mobile device using a biometric. This means most enterprise employees will allow solutions like TraitWare to create more efficient, more secure, modern authentication.
The TraitWare solution makes it simple, with patented authentication technology that leverages the user’s behavior in addition to their biometrics, which is entirely transparent and seamless to the user during login.
Perceived Challenge 2:
Many organizations are wary of the accuracy of biometrics and fall back to PIN codes and passwords to avoid users being locked out of their accounts.
Facts:
TraitWare uses only the most accurate biometrics provided by device manufacturers, ensuring both the security of the biometric used and the accuracy. For users who do not wish to use a biometric, or for those who are unable to use one, TraitWare also offers PhotoAuth®, an image-based PIN that is more secure than a traditional numeric PIN.
Multiple authentication methods can be combined to provide password elimination that’s both convenient and more secure.
Perceived Challenge 3:
When devices are replaced or upgraded, data doesn’t get transferred.
Facts:
While passwords may seem like the easiest and most convenient way to accomplish device replacements, the process opens up risks for bad actors to register replacement devices and hijack user accounts. In addition, having to re-register at every service provider makes the recovery or phone replacement process extremely cumbersome.
TraitWare® suggests that an admin ‘proof’ the identity of the user who needs to replace the device, in order to make sure they really are the person requesting the recovery. This can be done in a number of ways, such as over a video call or a known identity on a business chat service. The admin can then issue that user a new registration code for their new device. With a couple of touches, the user is back up again with immediate access to their resources.
Perceived Challenge 4:
Passwords Are Embedded In Legacy Systems
It’s Too Difficult and Too Costly to Change to Passwordless
Most legacy systems use old protocols, such as RADIUS (built in 1991) which require passwords. These older systems are difficult to manage and maintain, and typically use an organizational identity store like LDAP for password authentication. In this case, the identity store needs to continue to support passwords as long as legacy systems are in place.
Many organizations stop here because they aren’t aware of solutions that eliminate passwords without having to touch the legacy system.
Facts:
TraitWare’s passwordless solution does not require a legacy system and will be up and running in one day. The cost of implementation and use is less than the cost required to maintain legacy systems. And, you’ll save 60% or more on support budgets, plus increased productivity with no downtime for password recovery.
Perceived Challenge 5:
Today, many organizations are required to use multi-factor authentication to comply with security and privacy regulations. The most popular way to address multi-factor authentication (MFA) is to keep password-based credentials then implement another factor on top of it such as email-based one-time codes.
Facts:
Layering MFA over a legacy login method compounds the problem and increases friction for the user.
With less effort, organizations can deploy a completely Passwordless solution that’s more secure and more convenient. TraitWare is Real MFA and SSO combined for a friction-free user experience.
Perceived Challenge 6:
Passwords are most easily integrated with Existing Identity Infrastructure
Facts:
The more you rely on passwords, the harder it will be to get rid of them in the long run. And, there will come a time when we no longer use them, due to the associated security risks.
The latest identity and authentication technologies, like TraitWare’s patented MFA + SSO solution, are far more secure and easier to integrate and maintain. And, it’s not as big of a leap as you might think!
It’s time to fix a legacy problem with modern technology. Ready to see it for yourself? Want to hear more? Contact us anytime, book a demo, or start your free trial today!