
Enterprise Cybersecurity: Practice vs. Risk
Are We Getting It Wrong? Due to the rising severity and frequency of cyber-attacks, Enterprise spending on cybersecurity is also rising worldwide. But debate is heating around which security methods we should employ. Where are organizations focusing their efforts, and where is the most risk? According to experts, companies may not be getting their priorities […]

Should Governments Require Stronger Security?
Rising cyber threats and incidents of cyber-attack across the globe have many calling for federal intervention to protect our digital valuables. What’s Happening … In recent news, the United Health Group (UHG) paid a $22 million ransom to the BlackCat ransomware gang for a late February cyber-attack on subsidiary Change Healthcare. The attack, which was […]

The Problem with Passkeys
There has been a lot of talk about Passkeys. Are they right for you and your company? Why the pushback? Let’s have a look. What are Passkeys? Passkeys are credentials that replace passwords, relying on public key cryptography based on the WebAuthN protocol. The public key is stored with the company that creates your account, […]

Privacy & Cybersecurity Compliance Deadlines – 2024
What Privacy and Security Mean for Companies With Data Privacy Week coming up soon, we’re thinking about the important symbiotic relationship between privacy and security, and ahead to some pending deadlines for cybersecurity and privacy compliance. How can company leaders best navigate the waters and enjoy peace of mind? Here are a few upcoming privacy and security […]

Improved Cybersecurity and Ease of Use for MSPs
TraitWare, pioneering modern Passwordless Multi-Factor Authentication (MFA) and adaptive Identity and Access Management (IAM) has announced its strategic partnership with the Acronis CyberApp platform, revolutionizing cybersecurity for Managed Service Providers (MSPs) and their customers. This collaboration will deliver cutting-edge Phishing-Resistant Passwordless MFA and Single Sign-On (SSO) capabilities to Acronis MSPs, to reduce cyber risk and […]

Cyberattack: Where the Blame Goes. And Where Kudos Belong
There have been so many articles and posts about the recent Securities Exchange Commission (SEC) lawsuit against SolarWinds and their #ciso – and plenty written about recent breaches via the Okta platform. So much has been said about how attackers used social engineering to lure users to give up information or reset accounts. … Still, I feel like […]

Cybercrime in Schools
WHY SCHOOLS ARE PRIME TARGETS FOR CYBERATTACK, AND HOW WE CAN DO BETTER TO PROTECT THEM The University of Michigan was in the news recently following a cyberattack that caused an internet outage across all campus networks, eventually requiring password resets for all users. This is just one event amid a series of cyberattacks on […]
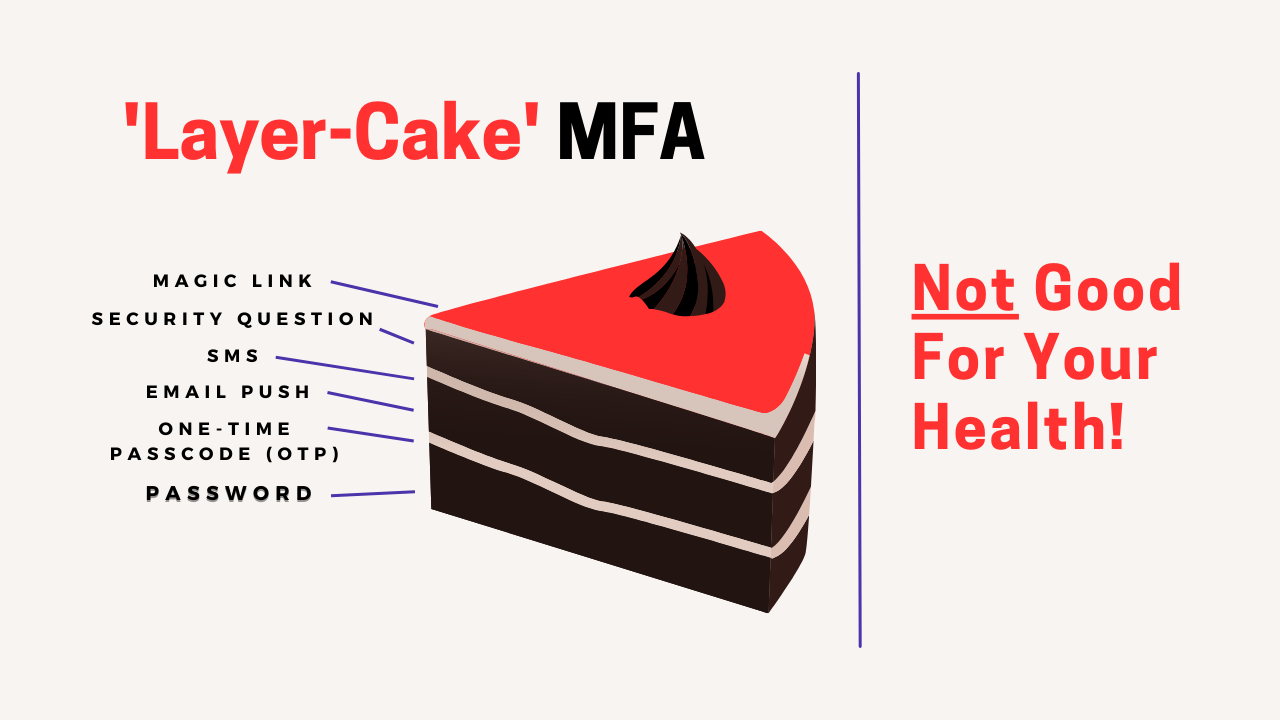
MFA and the Truth About ‘Layered’ Security
Multifactor Authentication (MFA) and Layered Security have long been recommended best practices for enterprise security. But what exactly are they? … At what point are there too many layers? And WHICH layers of security should I deploy? What is Layered Security? Layered security attempts to secure organizations by employing various tools – ideally complementary tools. […]

The LastPass Lockout and the Lessons learned from it
Angry LastPass users have taken to social media with reports that they’ve been struggling to access their accounts since the company’s security upgrade back in May. What’s more, there doesn’t seem to be a simple solution in sight. What does this have to do with MFA? The trouble began on May 9, 2023, when LastPass […]

Supply Chain – Connectivity, and Best Practices for Cybersecurity
The digital age has brought radical change to many industries. And, as the world becomes increasingly connected, long and complex supply chains are common for companies of all sizes. While connectivity has been good for international commerce, it also comes with elevated risk – particularly for the supply chain. Regardless of size or industry, cybersecurity […]

What has happened in cybersecurity since Biden called in 2021?
Two years ago (August 25th, 2021) business leaders – including some of Silicon Valley’s biggest Tech players, water and energy companies, banking and insurance firms, and academic institutions – were summoned to the White House to discuss one of the world’s most pressing concerns: Cybersecurity. The meeting came in the wake of several cyber-attacks – […]

TraitWare Patents
TraitWare’s patented innovation is part of what makes us stand out from the competition. Find out more about our unique technology. Patented Innovations (6 Granted)* Patents Pending *US patents (101649740, 1050388, 11068476, 11301555, 11406196, 11805121) Selected TraitWare processes (such as registration, Windows authentication, and Linux authentication) are also covered by pending US and international patent […]