
6 Mistakes to Avoid When Deploying Multi-Factor Authentication
The combination of username and password is no longer enough to secure your data. This is why multi-factor authentication (MFA) is being adopted by a growing number of organizations and businesses. The goal of MFA is to throw three or more hurdles at cybercriminals to deter them from pursuing access to your network to get […]

4 Technologies to Improve Your Security
For security teams, the COVID-19 pandemic either introduced new challenges or magnified old ones. Because of this, many organizations are assessing new security technologies or speeding up the deployments of others, which have already been in the works. For businesses, the pandemic has made it necessary for security teams to protect widely scattered endpoints and […]

How to Avoid SSO Implementation and Management
By allowing users to execute a master sign-on to authenticate themselves, single sign-on (SSO) improves user experience in terms of convenience as well as security. However, while SSO takes away the hassle with logins, successful implementation requires diligent management and the proper tools. Because the truth is implementing SSO requires some work and an unerring […]

Why Multi-Factor Authentication Is Essential for Healthcare
Security and data breaches are a major concern for every organization. Companies in the healthcare sector are especially vulnerable: they are a top target for cybercriminals because the black market value of medical data is exceptionally high. According to Experian, medical data sells for more on the dark web than credit card information or other […]

How Can You Optimize Passwordless Authentication?
Have you gone passwordless yet? Making the switch may be the best security move you can make today, because passwords are becoming even less secure, especially when you consider users’ tendency to have poor password security habits. For example, 52 percent of users reuse the same password for multiple accounts, and 59 percent of American […]

ZeroTrust and work from Mars, By Chris Werpy, COO, PlanetOne
As our Planet made the shift to work from wherever, remote access exploded in numbers and speed, with capacity taking the lead. Looking ahead, it’s time to determine how to not only keep the lights on, but to drive increased productivity without compromising security. Is the environment we work in today designed for the future, […]

Why Companies do not want to Go Passwordless
Addressing the Top 4 Reasons for Hesitation Studies have shown an increased appetite among consumers for multi-factor authentication, including biometrics as a replacement for the username and password login method, and evidence is clear that credential-based login poses the number one threat for security breaches. Experts and tech writers have been saying that we need to “break […]

Cyber Resiliency for Small Businesses: Techniques and Tips
Cyber Resiliency for Small Businesses: Techniques and Tips In the context of cybersecurity, resiliency is all about how organizations bounce back from an incident that involves the interconnection of multiple domains such as cybersecurity, business continuity, and organizational operations. You need to be cyber resilient to adapt and continue to deliver services or provide products […]
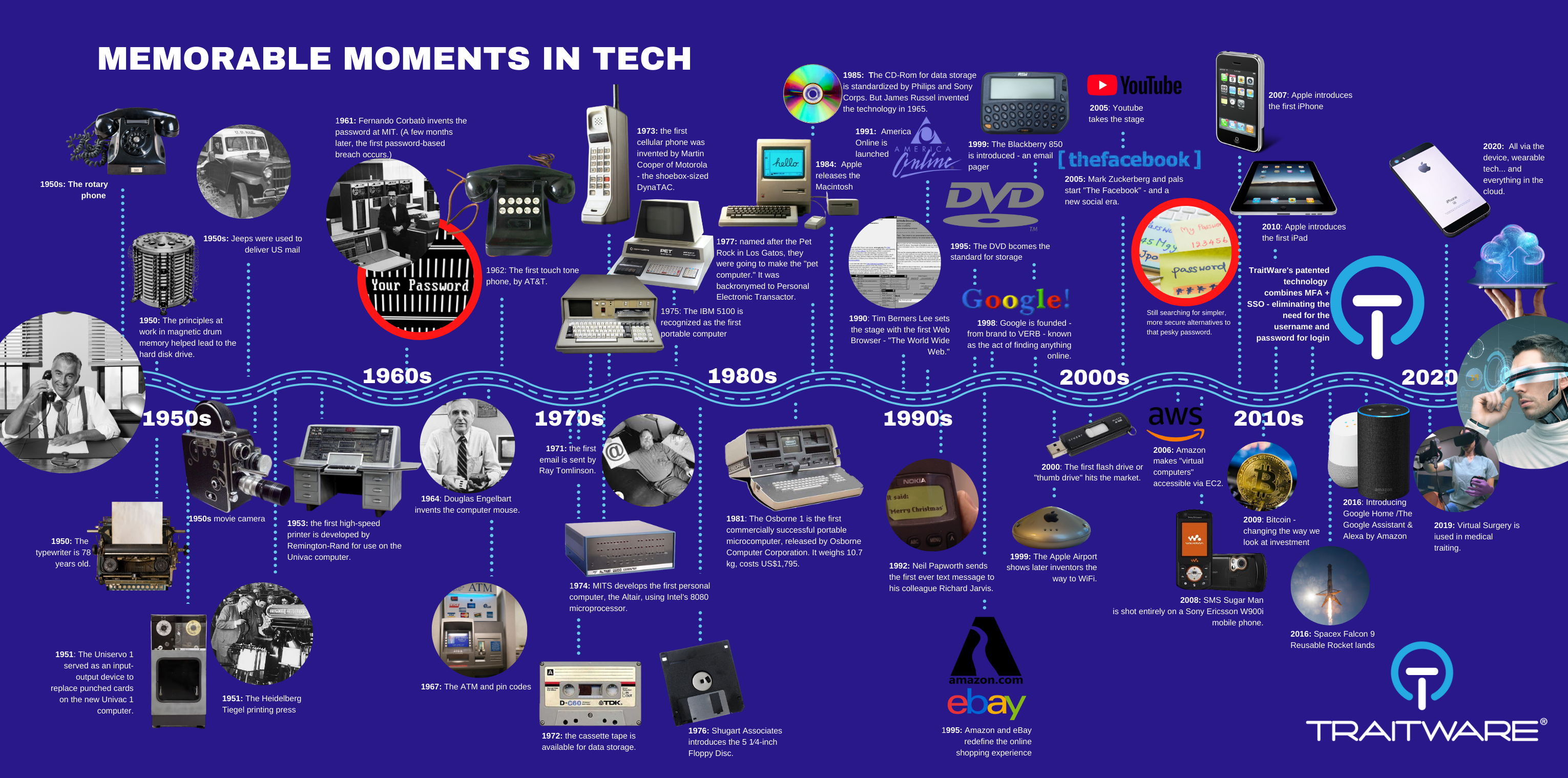
How Tech has Evolved. And How it Really Hasn’t.
It’s Time to Fix What’s Been Broken From the Get-Go As humans, we’ve evolved a fair amount. But Technology is another animal altogether. Taking a look at our infographic, the technological shifts we’ve witnessed since the 1950s are nothing short of mind-blowing. From pen and paper and a phone to today’s superpowered mobile devices, AI, […]

Beware of Tycoon – the Ransomware Targeting Windows and Linux Systems
Beware of Tycoon—the Ransomware Targeting Windows and Linux Systems. Windows and Linux systems are in the cyber-crosshairs of a recently uncovered ransomware, in what appears to be a targeted campaign. Tycoon is a multi-platform Java ransomware that is deployed in the form of a Trojanized Java Runtime Environment (JRE) and leverages an obscure Java image […]

Best Practices for SMEs’ Data Security
Data Security at SME’s are targeted by cyber attackers for their lack of resources or expertise to effectively protect their data. Managed security services provider Alert Logic estimates that small businesses make up 58% of malware attack victims, and that 94% of these attacks are carried out through malware or phishing emails disguised as bills, […]

How to get Free Passwordless Login Security
TraitWare® offers FREE Passwordless Login Security to Citrix customers First and foremost, the health and safety of friends and families takes precedence. With the developing changes surrounding the COVID-19 emergency, companies are adopting rapid procedures to help protect their employees. The most immediate change that most companies are adopting is a shift to working remotely. […]