
The CDK Global Data Breach
A Worldwide Wake-Up Call Last week, automotive software-as-a-service (SaaS) provider CDK Global reported a Data Breach that has had ongoing catastrophic effects on the company, its customers, and consumers. While the event has devastated the dealerships, the story is a worldwide wake-up call for all. What happened? What are the effects? What can affected companies […]

October is Cybersecurity Awareness Month!
As 2023 Champions, we’re sharing our Top 4 Tips to Stay Safe Online ** For more information on simple steps you can take toward maximum security for your company, contact us any time.
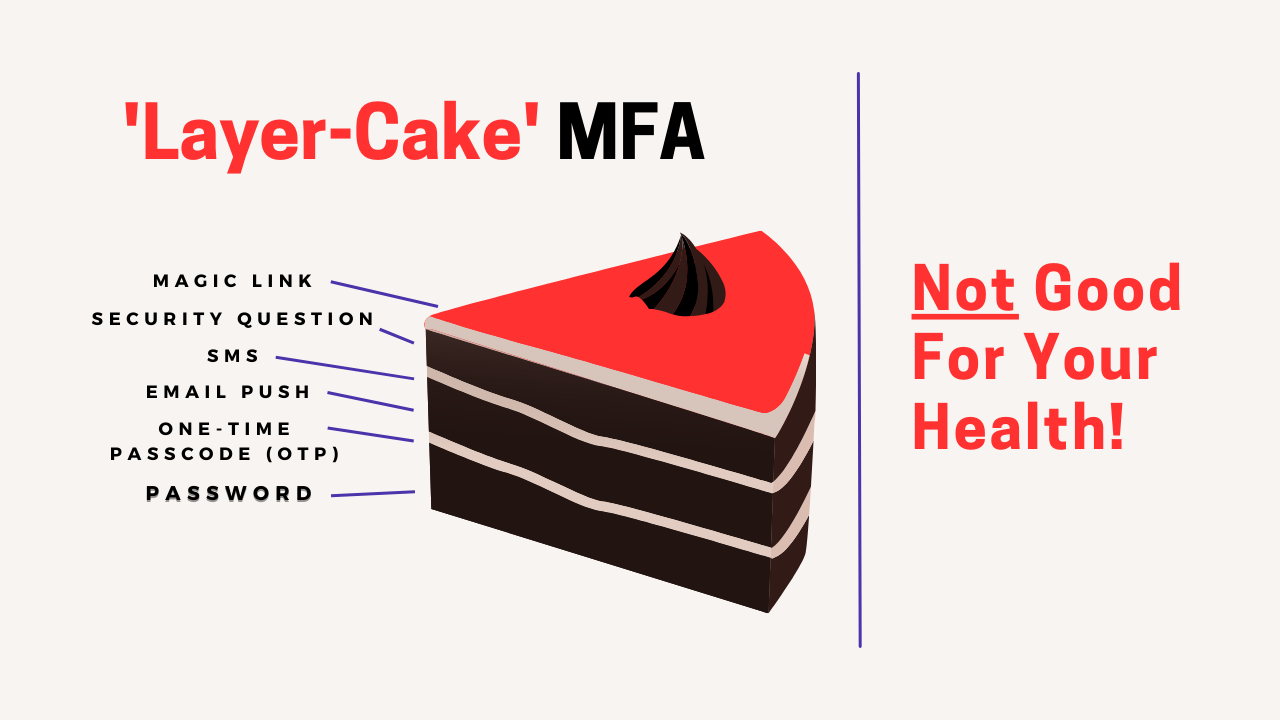
MFA and the Truth About ‘Layered’ Security
Multifactor Authentication (MFA) and Layered Security have long been recommended best practices for enterprise security. But what exactly are they? … At what point are there too many layers? And WHICH layers of security should I deploy? What is Layered Security? Layered security attempts to secure organizations by employing various tools – ideally complementary tools. […]

The LastPass Lockout and the Lessons learned from it
Angry LastPass users have taken to social media with reports that they’ve been struggling to access their accounts since the company’s security upgrade back in May. What’s more, there doesn’t seem to be a simple solution in sight. What does this have to do with MFA? The trouble began on May 9, 2023, when LastPass […]

Supply Chain – Connectivity, and Best Practices for Cybersecurity
The digital age has brought radical change to many industries. And, as the world becomes increasingly connected, long and complex supply chains are common for companies of all sizes. While connectivity has been good for international commerce, it also comes with elevated risk – particularly for the supply chain. Regardless of size or industry, cybersecurity […]

What has happened in cybersecurity since Biden called in 2021?
Two years ago (August 25th, 2021) business leaders – including some of Silicon Valley’s biggest Tech players, water and energy companies, banking and insurance firms, and academic institutions – were summoned to the White House to discuss one of the world’s most pressing concerns: Cybersecurity. The meeting came in the wake of several cyber-attacks – […]

5 Myths Around Single Sign-On
There are many misperceptions around Single Sign-On (SSO) – all of which need addressing. 5 MYTHS AROUND SSO – BUSTED: 1. SSO is not secure because if a user’s master password is compromised, an attacker could have access to all user accounts. BUST: SSO actually enhances security by reducing the number of passwords a user must […]

What is the FTC Safeguards Rule? And Will it Affect You?
What is the FTC Safeguards Rule? In 1999, The Federal Trade Commission (FTC) initiated The FTC Gramm-Leach-Biley Act’s (GLBA) Safeguards Rule in an effort to safeguard consumers and protect personal information from getting into the wrong hands. FTC Summary: “The Safeguards Rule requires financial institutions under FTC jurisdiction to have measures in place to keep customer […]

Norton LifeLock and LastPass: Doubt about Password Managers Security
But are the Wrong Questions Being Asked? Recent news of cyber-attacks on two major security companies has many asking, “Are password managers secure enough to protect our data?” But perhaps there’s a more important question that needs to be addressed. This week, news came of a cyber-attack on Norton LifeLock. Several thousand customers were reportedly […]

October is Cybersecurity Awareness Month – 2022
Back to Basics Understand The Consequences, Reduce Risk, and Simplify Access with The Basics for Cybersecurity As proud Champions of Cybersecurity Awareness Month, we’re doing our part to help spread awareness about the need for proper cybersecurity hygiene, while offering enterprise-class solutions for enhanced security and simplified user experience for greater adoption. The consequences […]

Enhanced Security and Simplicity for Software Development Community
Zero Trust Multi-Factor Authentication (MFA) and Single Sign-On (SSO) Combined for Seamless User Experience and Secure Access to GitLab RENO, NEVADA, USA, October 3, 2022 /EINPresswire.com/ — GitLab Inc., provider of The One DevOps Platform, and TraitWare Inc., providing native passwordless MFA and SSO for enterprise login, today announced their partnership, which delivers simpler, secure access for […]

CYBER INSURANCE WON’T PAY
Unless You Do These Things First Company budgets are now being firmed up for 2023 and, as the frequency, severity, and cost of cyber-attacks increase dramatically, it’s no wonder that enterprise demand for cyber insurance has also skyrocketed. But, while cyber insurance may seem like a relatively easy way for a company to plug in […]