
2FA is Not MFA: The Distinction Matters More than Ever
In the world of cybersecurity, experts talk a lot about Multi-Factor Authentication (MFA) as the #1 basic requirement for all Enterprises. Companies have a tendency to think of Two-Factor Authentication (2FA) as the same as MFA. But the Truth Is: 2FA is not MFA, and treating them as interchangeable is a dangerous misconception—especially for businesses […]

Security Doesn’t Matter
It’s About Your Bottom Line Let’s be honest—no one wants to talk about cybersecurity. It’s boring. It’s complicated. And for most business leaders, it’s an afterthought. What really matters? The bottom line. CEOs, CFOs, and decision-makers aren’t losing sleep over how many authentication factors their employees use. They’re worried about revenue, operational costs, and profit […]

AI vs. AI / Fighting AI with AI in Cybersecurity
The Rise of AI-Powered Cyber Attacks Cybercriminals are increasingly leveraging artificial intelligence (AI) to launch sophisticated attacks. From AI-generated phishing emails to deepfake social engineering scams, traditional security methods are struggling to keep up. To combat this growing threat, businesses must fight AI with AI, deploying advanced security solutions that detect, analyze, and neutralize AI-driven […]

How to Phish-Proof Your Login
Across the Enterprise You’ve heard it before: Phishing is the #1 method used by cybercriminals to gain access to your digital valuables. Today, according to CSO Online, 80% of reported security incidents are caused by Phishing. We’ve also heard from CISA and others that MFA is the holy grail for cybersecurity. But then last week, […]

The CDK Global Data Breach
A Worldwide Wake-Up Call Last week, automotive software-as-a-service (SaaS) provider CDK Global reported a Data Breach that has had ongoing catastrophic effects on the company, its customers, and consumers. While the event has devastated the dealerships, the story is a worldwide wake-up call for all. What happened? What are the effects? What can affected companies […]

Keep it Simple: Go Passwordless
People like Matt Topper are helping to spread the word. The story of the password is worth telling … again. Because P@$$w0rD$_suçK! Once upon a time, in 1961, man invented the Password for digital security. Back then, there was a thing called the “perimeter” where company digital assets resided. The password was the “key” that […]
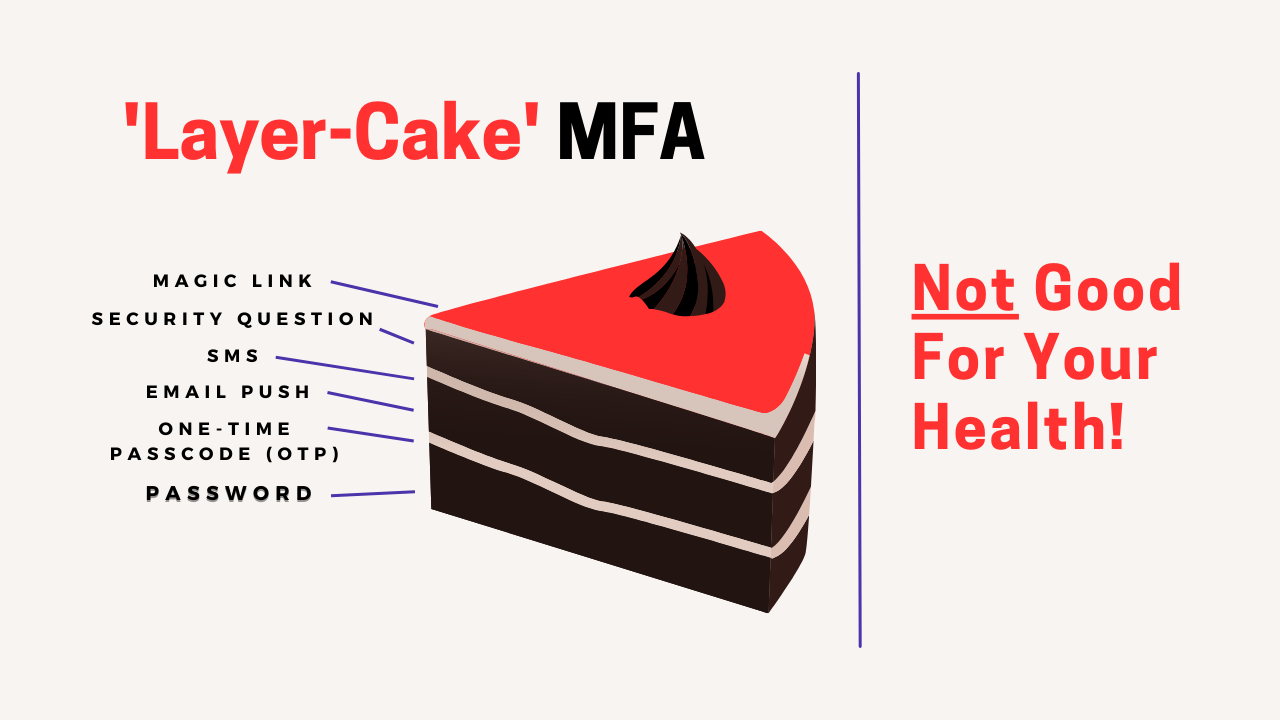
MFA and the Truth About ‘Layered’ Security
Multifactor Authentication (MFA) and Layered Security have long been recommended best practices for enterprise security. But what exactly are they? … At what point are there too many layers? And WHICH layers of security should I deploy? What is Layered Security? Layered security attempts to secure organizations by employing various tools – ideally complementary tools. […]

Zero Trust is No Silver Bullet
Zero trust is the Buzzword for cybersecurity today. As a result, the market is brimming with “zero trust” solutions. What is it exactly? What solutions should you choose? Making sense of it all, for any company, can be a daunting task. But what’s more, as experts and leaders continue to urge businesses to move to […]

TraitWare’s Passwordless MFA Secures Place in the Financial Sector
TraitWare MFA selected to Secure Federal Credit Union

Why Experts Urge All Businesses to Strengthen Cybersecurity Now
Multi-Factor Authentication is Top Priority In light of current world events, experts are urging businesses of all sizes to bolster security, with Multi-Factor Authentication (MFA) as top priority for the protection of our digital assets. While conflict may seem far away for most of us, the reality is that cyberspace knows no borders – and […]

LastPass Says No Passwords Compromised in Security Scare …
But you should ditch that master password anyway. And it’s easier than you may think. Last week Tuesday, another security scare hit cyberspace and password manager LastPass. The scare points, once again, to the fact that passwords are risky. Several users reported receiving email alerts from LastPass, warning that unauthorized attempts had been made to […]

BACK TO SCHOOL FOR CYBERCRIME WITH TRAITWARE.
Schools are top targets for Cybercrime. It’s time to get educated and educate about the risks, and how to implement a Zero Trust framework for security. With students of all ages still in the early days of their academic year, cybersecurity experts issue stern warnings about cybercrime in schools. With the increased use of technology […]